Turn on IP whitelist in Vicidial with the easy way.
How to – Turn on IP whitelist in Vicidial
Step 1 – Enable IP List
Login to the admin panel and then go to system settings
Admin -> System Settings
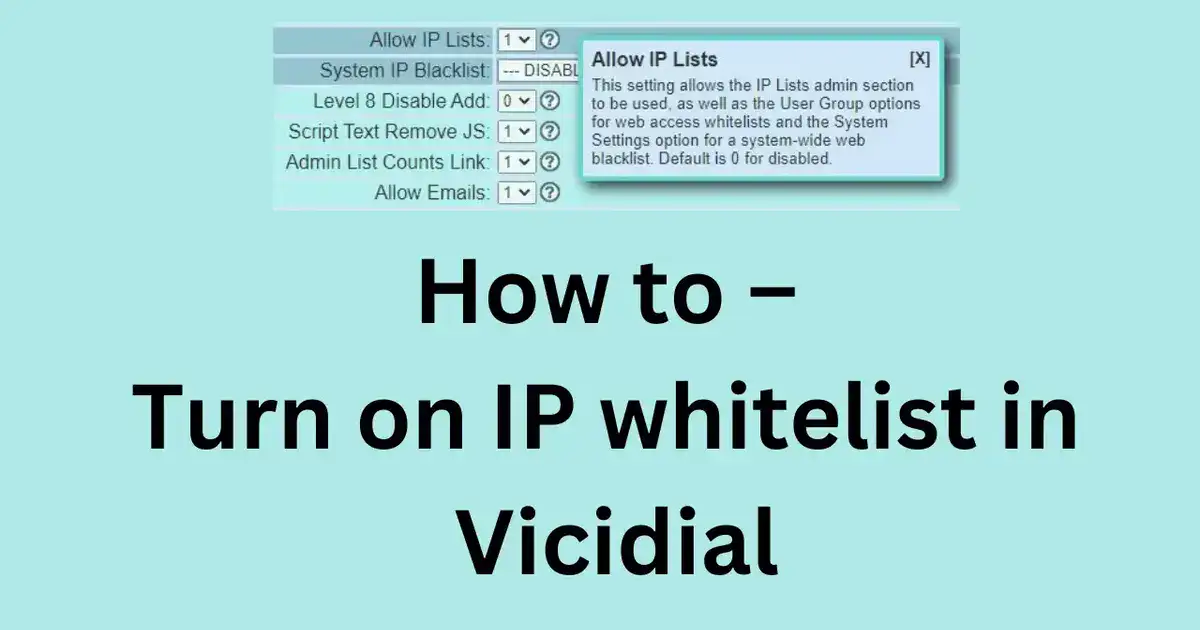
Scroll down to “Allow IP Lists” and enable it by setting it to “1”
Step 2 – Go to the Admin user(6666) and enable access
Go down to the bottom of the user setting screen and set “Modify IP Lists” to 1(good idea to ignore ip list for yourself)
Step 3 – Turn on whitelist for the user groups you want to limit access
Go to user groups > scroll down to whitelist settings
Turn on IP whitelist in Vicidial
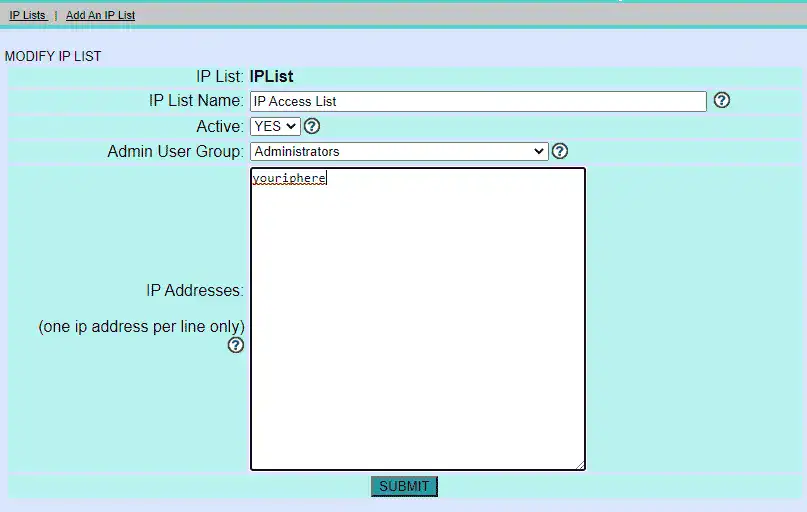
Step 4 – Go back into admin section and click IP Lists to add IP’s
Click IP lists
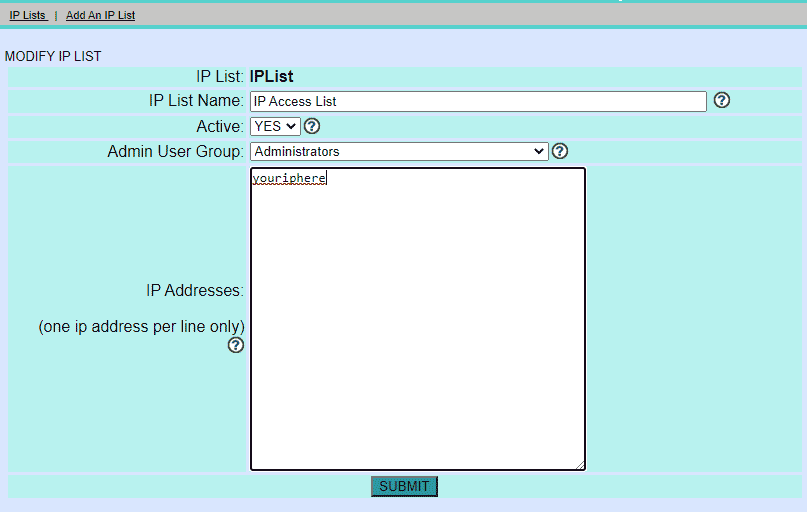
Make sure to add your IP’s to the list
Thats it, you have now enabled IP whitelist access only. Make sure to update your crontab entries for
VB-firewall.pl from –blacklist to –whitelist=ViciWhite
and such like so:
Your IP list configuration is now finely tuned, whether you choose to embrace the sanctuary of whitelisted IPs or take a firm stance against unwanted or potentially harmful traffic infiltrating your Vicidialer. Should queries linger in the corridors of your mind, feel free to reach out to us at [email protected]
in Vici Box there is similar method which I believe to share here
In the realm of Vici Box, a comparable method beckons, and it’s a knowledge nugget I’m eager to share.
Banish the notion of commencing from absolute scratch; commence with the standard Vicibox as your canvas. Navigate through the intricacies via the “yast firewall” avenue. Here, the strategic move involves deactivating all sanctioned services and unearthing open ports.
What transpires is a realm where “nobody is allowed in,” providing you the canvas to selectively admit IPs under the “custom” umbrella. Tailor your allowances, encompassing both TCP and UDP for agent IP locations, reserving TCP exclusively for administrative screens, and allocating UDP solely for the domain of “just phones.
“However, a caveat stands—remember to disable ping. While nestled within a configuration file, its influence may also lurk within the realms of yast, though this is a path we’ve yet to traverse (opting to navigate the config file directly).
Feel the assurance of a system sculpted to your preferences, where access is a privilege granted with discernment.